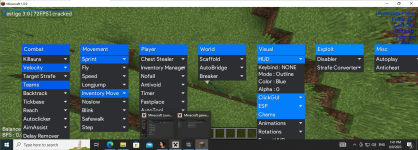
Client Vestige 3.0 beta 9 hotfix crack
- Thread starter tear
- Start date
sus13122004
Member
skid
mit sieubeo
Member
- Joined
- Jul 23, 2023
- Messages
- 47
- Reaction score
- 2
- Points
- 8
yess crack
prove it retardCrazy rat
Did you do like partial deobf on this? There's no way the client's this badly protected normaly lol
Java:
Object something = new Object("something");
Java:
Object something = new Object(this.lol());
public void lol() {
return "whatever";
}Strong obf $$
Last edited:
Its using self made encryptionDid you do like partial deobf on this? There's no way the client's this badly protected normaly lol
->Java:Object something = new Object("something");
Java:Object something = new Object(this.lol()); public void lol() { return "whatever"; }
Strong obf $$
Basically strings were encrypted and decryption keys were given by the server
So I made a transformer to deobfuscate that shit
I’ll post transformer soon
Also tear account is a troll acc and is made by me
That's hillarious xdBasically strings were encrypted and decryption keys were given by the server
Java:
package uwu.narumi.deobfuscator.transformer.impl.vestige;
import org.objectweb.asm.tree.*;
import uwu.narumi.deobfuscator.Deobfuscator;
import uwu.narumi.deobfuscator.transformer.Transformer;
import javax.crypto.Cipher;
import javax.crypto.spec.SecretKeySpec;
import java.lang.reflect.Modifier;
import java.nio.charset.StandardCharsets;
import java.security.MessageDigest;
import java.util.Arrays;
import java.util.Base64;
import java.util.regex.Matcher;
import java.util.regex.Pattern;
public final class VestigeEncryptionTransformer extends Transformer {
// put decryption keys there (sent by the server, so we need to hardcode)
private static final String[] DECRYPTION_KEYS = {
};
@Override
public void transform(Deobfuscator deobfuscator) throws Exception {
for (ClassNode cn : deobfuscator.classes()) {
a:
for (MethodNode method : cn.methods) {
if(!Modifier.isPublic(method.access) || !method.desc.equals("()Ljava/lang/String;")) {
continue;
}
String string = null;
int ldcCount = 0;
for (AbstractInsnNode insn : method.instructions.toArray()) {
if(insn.getOpcode() != LDC) {
continue;
}
LdcInsnNode ldc = (LdcInsnNode) insn;
ldcCount++;
if(!(ldc.cst instanceof String) || !isBase64Encoded((String) ldc.cst)) {
break a;
}
string = (String) ldc.cst;
}
if(ldcCount != 1 || string == null) {
continue;
}
String decrypted = null;
for (String decryptionKey : DECRYPTION_KEYS) {
try {
decrypted = decryptString(string, decryptionKey);
break;
} catch (Exception ignored) {
// we believe in allah for no unexpected error
// this should be called if we are using the wrong decryption key
;
}
}
if(decrypted == null) {
System.err.println("Class node " + cn.name + " method " + method.name + method.desc + " couldn't be decrypted. Probably not a getter for encrypted string.");
continue;
}
InsnList list = new InsnList();
list.add(new LdcInsnNode(decrypted));
list.add(new InsnNode(ARETURN));
method.instructions = list;
}
}
}
private String decryptString(String string, String decryptionKey) {
try {
byte[] a = decryptionKey.getBytes(StandardCharsets.UTF_8);
MessageDigest messageDigest = MessageDigest.getInstance("SHA-1");
a = messageDigest.digest(a);
a = Arrays.copyOf(a, 16);
Cipher cipher = Cipher.getInstance("AES/ECB/PKCS5Padding");
cipher.init(Cipher.DECRYPT_MODE, new SecretKeySpec(a, "AES"));
return new String(cipher.doFinal(Base64.getDecoder().decode(string)));
} catch (Exception ex) {
throw new RuntimeException(ex);
}
}
private boolean isBase64Encoded(String input) {
String base64Pattern = "^(?:[A-Za-z0-9+/]{4})*(?:[A-Za-z0-9+/]{2}==|[A-Za-z0-9+/]{3}=)?$";
Pattern pattern = Pattern.compile(base64Pattern);
Matcher matcher = pattern.matcher(input);
return matcher.matches();
}
}Before deobfuscationDid you do like partial deobf on this? There's no way the client's this badly protected normaly lol
->Java:Object something = new Object("something");
Java:Object something = new Object(this.lol()); public void lol() { return "whatever"; }
Strong obf $$
It also looks like the encryption/decryption class is hardcoded in vestige source code lol
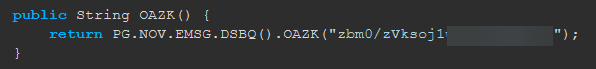
So the only thing you did was reverse a string obf with a hard coded key? lmaoBefore deobfuscation
It also looks like the encryption/decryption class is hardcoded in vestige source code lol
View attachment 799
ExStack
Active member
- Joined
- Dec 17, 2021
- Messages
- 137
- Reaction score
- 23
- Points
- 28
1920x700 goes
I'm not sure but I think each jar is encrypted with different keysSo the only thing you did was reverse a string obf with a hard coded key? lmao
it's a vm1920x700 goes